Tools I used:
1. Hex Editor (I Recommend HxD http://mh-nexus.de/en/downloads.php?product=HxD)
2. PEditor by yoda&M.o.D. ( PEditor )
3. Ollydbg ( http://www.ollydbg.de/download.htm )
I will follow the below steps:
1. Find a dummy image to use it’s raw data… (1)
2. Find an executable with virus
3. Check the results in VirusTotal..
4. Modify the PE Header of infected executable, to add a new segment
5. Select some data from the image file (1) and add them in the new segment
6. Encrypt permanently the original segments
7. Inject some code to make the XOR decryption using olly to check step by step the execution flow
8. Confirming that exe is working fine, and upload to VirusTotal to check for the new results 😀
1. Find a dummy image to use it’s raw data
Well, this is easy.. Let’s use google to search an image… What i searched is “virus” 🙂 Now we have to select an image with complexity.. It has to be a bit complex, cos if you think the jpeg contents, they have to be as much complex as they can, in order not to be a repeatable pattern.. So i select this image for the example http://www.healthinitiative.org/IMAGES/virus_big.jpg ..it has some complexity but not so much.. anyway i like this image 😀 ..Also think that u can use a fractal image.. it gonna give you a cool complexity! 😉
2. Find an executable with virus
These days i receive a spam from a brazilian friend (who is infected with the virus) with a trojan executable.. A quick analysis of this will be presented in a future post, cos atm is still active, and victim’s personnal info (user;pass) are available publicly…. The executable is packed with ASPack.
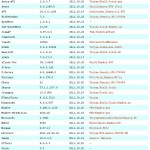
3. Check the results in VirusTotal
Uploading that executable to VirusTotal I take the following results
4. Modify the PE Header of infected executable, to add a new segment
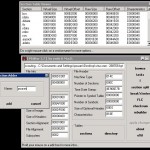
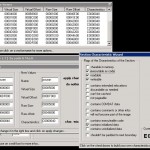
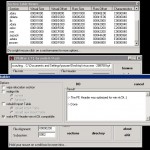
Using the PEditor by yoda, (I use this tool years now it’s the best) we will add a new segment in the executable so we will be able later to store data, and some injected executable code.. This will be our “storage” in the exe file.. I add a segment with name “pouran” doing the following : opening the exe with peditor :p – click ‘sections’ button – click on any existing section, select add a section and i entered ‘pouran’ as name – then on the new section clicked ‘edit section’ and changed the virtual size to 00005000 (means 0x5000h=20.480 bytes) i think it’s enough size for some data.. – press ‘char. wizard’ to enable the execution flag to the section.. Now we have to realign the header sizes (else we’ll have a ‘not valid win32 application’ message) – click button ‘rebuild’ and check only ‘make win compatible’ and press DO. Screenshots below shows these operations :
5. Select some data from the image file (1) and add them in the new segment
7. Inject some code to make the XOR decryption using olly to check step by step the execution flow
Here is the final step needed in order to have an executable ready to run and decrypt itself on runtime.. I’ll follow these steps :
1. I insert 100h bytes in the section added, so we can inject the executable decryption code.. (we could find another place in the executable ok.. but i prefer this) After adding the 100h bytes, I also align the ImageSize+100h and the Raw and Virtual size of the section +100h
2. Changed the Original Entry Point (OEP), from ASPack’s section, to my new section (in the beggining of the code injected)
3. Code is similar code used for the encryption, but the values in stack will be hardcoded, and pushed.. Also there is code aligning the stack.. In the beginning and in the end of code, there is pushad/popad in order to leave registers untouched.. After aligning the stack, I jump to the OEP.
Watch the video…. :
8. Confirming that exe is working fine, and upload to VirusTotal to check for the new results 😀
Now the time has come… I’ll upload the encrypted and self-decrypting executable to VirusTotal for check but 1st i have to run it to ensure it’s running ok… But remember!! : I encoded only 1 section… the section with the biggest size.. and the section with the code (.text is always the code section…) So we expect most of the AV to be bypassed.. but there are some that will catch the virus this time also.. why? but ofcourse cause i encrypted only the 1 section.. YOU can encrypt the others too with the same logic .. I leave this exercise to you..! 😉
Watch the photos below, after uploaded the self-decrypted virus to VirusTotal… :



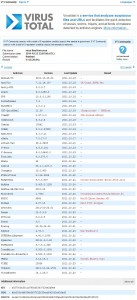
Nice and clean example…
Thank you for sharing ,,,,,!
you can automate this with metasploit. it is a great article.
@silentmouji
Yep ofc you can.. But msf will produce “recognisable” code.. but anyway i wrote this to show how somebody can write his own encryptor and be unique 😉 ..I wanted to show what’s behind that “automation” 🙂
Pingback: 133tsec.com » PoURaN PE-Encryptor: A XOR based encryptor injecting code to EXE/DLL files..Full C/ASM source available.
I suggest adding a “google+” button for the blog!
Hellen
@Elliptical Reviews
Thanks Hellen we just did.!!! 😉