Hello again.. There was a long time since my last post, cos i was busy with several issues, but most time with this tool.. Checking it’s operation, testing the hooked PE in different OSs, changing the method used, etc..
Finally i came up with this tool, and below i will explain exactly how it works, give you the source code and a binary, and show you some applications of this tool with video and/or shots…
This is an API hooking tool, which uses the PE IAT patch method, and runs the payload, injecting the code in the PE permanently, changing the PE Header apropriately (section sizes, OEP, ..) The final executable produced (hooked, and code-injected) tested on most OSs:
- Windows 7 x64 – SUCCEED
- Windows 7 x32 – SUCCEED
- Windows 2008 x32 – SUCCEED
- Windows 2000 – FAILED (The VEH APIs not supported by OSs <= Win2k)
- Windows 2003 x32 – SUCCEED
- Windows XP x32 – SUCCEED
- MAC OS running wine – SUCCEED
Here is the tool! CPP Source with injected asm (i could say ASM with injected cpp 😛 ) and the compiled .exe .. if you don’t trust me to run binary 😛 just cl hooking.cpp /w and you got it 🙂
Hooking.zip – Get it!
What did I use to do it, was just some VMs to test it in different environments, and:
And ofcourse for the IAT and EAT of the PE Structure, I visited IcZelion’s guides (IAT, EAT) and used those methods in this tool.. Also I use the PEB method to obtain the Kernel Base in runtime on standalone codes, method used by most shellcodes.
Why whould you need an API Hooker ?? There are several reasons.. like :
- Backdoor files
- Change the API parameters on runtime
- Spy API execution on specific process
- etc
The method used from this tool, is physical modifying the Import Table of the PE, and patching/injection the user’s code so it is executed right BEFORE the API execution begins.. The tool just asks you which API you want to hook, and which is the file with the raw data (asm binary code) that will be inserted before the api execution.. The code that will be inserted must, for sure, be absolutely stand alone, what means that it must keep stack calibrated, must not refer to memory location out of the code (except from locals made in stack or imported functions from PEB) .. You have to know what you’re doing 🙂
BUT.. there is also another option of the tool. You can use the Exception Handling option.. which enables you to use code that may cause exceptions, code that does not manage it’s stack well, and maybe some 3rd party code.. This option, uses VEH (Vectored exception handling), installing the handler before your code execution, and removing the handler after the execution of your code, or after your code causes an exception.. Also the stack is being saved, so you dont have to care about the EBP and ESP values 🙂 The whole consept will be explained.
Here are two very nice and easy to understand API Hooking papers by Brian Mariani from High-Tech Bridge SA, published in exploit-db :
http://www.exploit-db.com/download_pdf/17802
http://www.exploit-db.com/download_pdf/17671
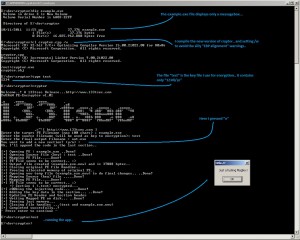
I will try to explain some basic things about how my tool is working. I hope you understand.. You can make your comments ofcourse! 🙂 Here are some Images about the operation.. :

Basic Hooking tool explanation
Continue reading →